AWS accounts & users: Separation of Concerns
Separating concerns is something we as developers are used to thinking about in terms of code. But the same also applies to identity management. If you’ve dabbled in AWS, you can get started right away with a root account. However, when it goes beyond dabbling, it might be a good idea to start splitting up responsibilities.
Since AWS is for the most part a paid service, it is recommended that you separate accounts based on what they need to do, if only for security’s sake. Personally I decided to make an Administrator account apart from my ‘root’ account. Any technical stuff I will do with the Administrator account, while I’ll save the root account for managing finances and delegating new users/roles through the IAM console.
Lately I’ve been using Terraform with AWS. Since Terraform only needs API access, it’s a good idea to restrict Terraform to an account with only ‘Programmatic access’, which will be one of the options when you make a new user with IAM. (See example)
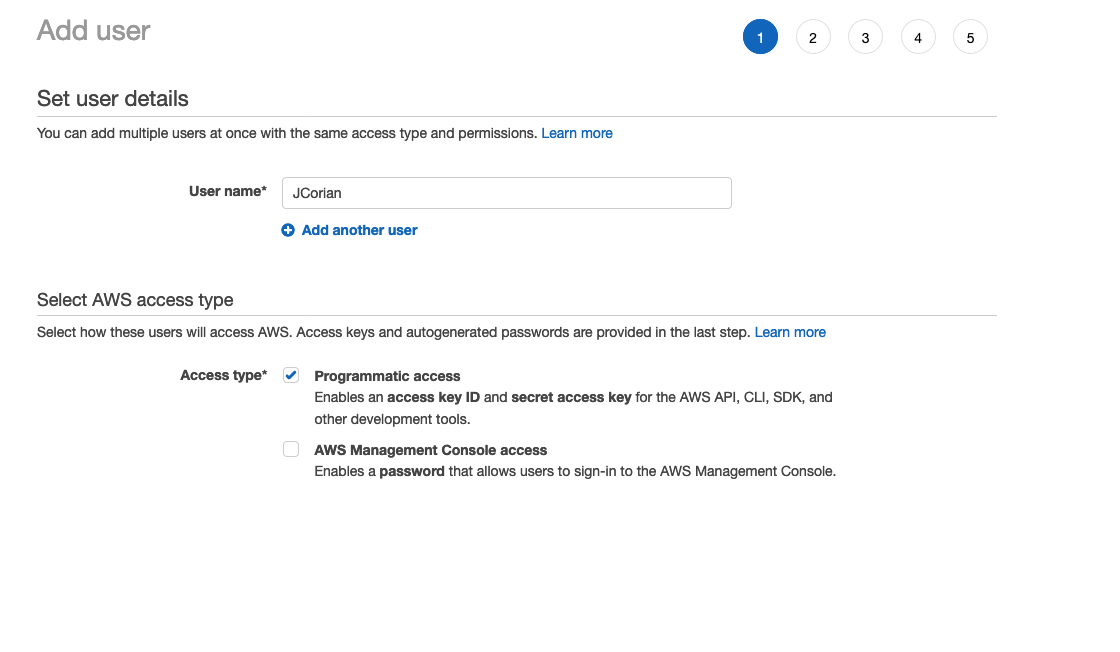
This is how I started my separated setup at AWS to prevent Terraform from having too many permissions and thought I’d share the concept. I hope it helps other developers think about IAM management in their AWS environments. Even though it’s just for hobby-projects for now 😉
Pro-tip: you can always go back and change privileges of a User (group)!
