How to hack a box - Introduction
Welcome to the blog series about how to hack a box! In this first post I’ll guide you through the global steps you can take to hack a box. The steps are universal, so you can use them on any target which you have permission for.
In the next few posts we’ll go through each step in detail and try to hack a box in Hack The Box, called Blocky.
| DISCLAIMER: Never attempt to execute one of these steps on a machine where you don’t have explicit permission for from the owner. This is illegal and will get you in trouble. |
Hack The Box
Hack the Box is a pen-testing lab where you have a huge fleet of machines at your disposal, with a difficulty ranging from Easy to Insane. They have several operating systems, mainly Linux and Windows, but Android as well. The goal is to capture two flags: the user flag and the root flag. To capture these flags, you’ll have to find your way into the box and eventually becoming root/Administrator.
The user flag can be found in /home/<some user>/user.txt for Linux, and C:\Users\<some user>\Desktop\user.txt.The root flag can be found in /root/root.txt for Linux, and C:\Users\Administrator\Desktop\root.txt.
|
To access a box, you need to install OpenVPN including the Hack The Box - Connection Pack (requires an account). After this, you need to claim the machine you want to use. Make sure you’re not choosing a machine which is already claimed by another user.
This box we’re going to hack is a retired box, which means two things: people are allowed to write a tutorial on how to hack it and you need to pay for a subscription of £10 per month to access the box. The subscription gives you access to all retired boxes. Non-retired boxes are free.
Preparation
Before we get started, let’s make sure we have the proper tools installed.
Kali Linux
I highly recommend using Kali Linux to walk through this series. You can simply install it in a VM. Do note you’re entering a network full of hackers. Though it is forbidden to hack users on the network, it could happen that a malicious user tries to break into your computer. For added safety, it is highly recommended installing Kali in a VM.
CherryTree
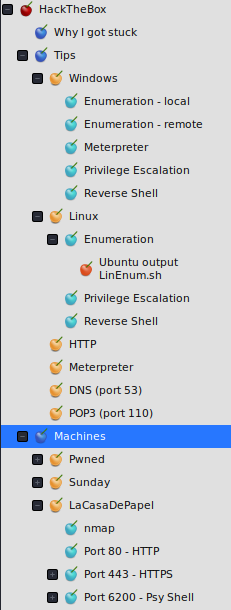
While going through the steps, you’ll encounter a lot of information which is good to write down. If you take notes, you can go through them without having to execute all kind of commands again. You can also save the output from scripts and screenshots of interesting things.
The tool I use for this is CherryTree. CherryTree is a hierarchical note taking application which is included in Kali by default. For every step I take, I note down the results. Basically it’s a structured write-up. Another thing I keep track of in CherryTree is my own pen-testing guide, based on OS and step and which port. Every time I learned something, I write it down in this guide. This way, I hopefully won’t make the same mistake twice. When I start on a box, I always start with creating a new entry for the machine in CherryTree.
Hosts file
To access a box easily, I always add an alias for the IP address in the form of <name of box>.htb in my hosts file. For Linux this is /etc/hosts and for Windows this is C:\Windows\system32\drivers\etc\hosts.
How to Hack a Box
Now we’ve got the preparation in place we can start with the steps. I myself use 4 steps when trying to hack a box:
-
Exploration
-
Gaining Access
-
Enumeration
-
Privilege Escalation
Let’s go a bit deeper into what these steps mean.
Exploration
When you start with a box, you only have the IP-address. A first step would be scanning which ports are open, finding out what software (and versions) run on them, and what you can see there. For example, if port 80 is open, you’ll browse through the website looking for interesting information. In this step you also try to collect all vulnerabilities that affect the software you’ve found, which you can try to exploit in the next step.
Gaining Access
After you’ve collected all the information, it’s time to try to get access into the box. The goal here is to get a shell in any form. This can either be SSH or a Reverse Shell.
To gain access, you’ll most likely exploit a vulnerability or using credentials you’ve identified in the previous step. Another possibility which you often see in Hack The Box or other Capture The Flags, is finding clues which lead to gaining access to the box.
Most of the time once you’ve gained access to the box, you can get the user flag without further steps.
Enumeration
Now we’ve got access to the box. The next goal is doing Privilege Escalation, but before we can do this we need to gather information on how to do this. Gathering information from the box is called enumeration. This includes gathering the OS and kernel versions, running processes, background tasks, users, interesting files, file permissions, open ports, etc. In addition, you’ll also look for Privilege Escalation[1] vulnerabilities in the software which is running on the box you might be able to exploit.
Privilege Escalation
After gathering all the information, we can try to escalate our privileges by using the information. Possible paths are misconfigured privileges, exploitable processes running as root or for example a Privilege Escalation vulnerability in running software.
To be continued
We’ve gone through the global steps of hacking a box. Each step can take a significant amount of time, depending on the difficulty and your own skill level. In my next blog post we’ll start hacking an actual box in Hack The Box, which is called Blocky.
Stay tuned!
