How to hack a box - Enumeration
Welcome back to the blog series about how to hack a box! In the past few blogs we’ve gone through a few steps which gives you an idea of how you can hack a box. We went from the Introduction, to Exploration, to Gaining Access. In this blog, we’ll cover the basics of Enumeration.
| DISCLAIMER: Never attempt to execute one of these steps on a machine where you don’t have explicit permission for from the owner. This is illegal and will get you in trouble. |
Enumeration
Enumeration is very similar to the exploration step: you’re gathering information about the system. Although this is a definition I use myself and is probably not an industry standard, the key difference between exploration and enumeration is you explore externally and enumerate internally.
Since we already have gained access to the target machine, our angle of attack is different when comparing to exploration. There’s still a lot of ground to cover though. We’ll focus on the basics for now, as advanced enumeration is a blog worth of its own. The goal here is gathering enough information to be able to Escalate our Privileges[1] on the Blocky box.
How to
There are a lot of things you want to check. A basic (not exhaustive) list which we’ll go through today:
-
Visible files to the current user
-
File permissions
-
Background jobs
-
Running processes and their owner
-
Open ports
-
OS and kernel versions
-
Access rights for the current user
For each item listed above, check if it’s a common item for the Operating System (OS).
You need to ask yourself if the item is (mis)usable.
For example you could think about a cron job running a Bash script as root every minute, while the Bash script is writeable by you.
Or a script which is executed by root and uses a wildcard as a parameter[2].
| Enumeration is only about gathering information, not altering the state of the machine by changing Bash scripts or running kernel exploits. |
You can use scripts to automate the process of enumeration a bit, but you still need to know what you are looking for and how you can do so. For me, this is still something I struggle with myself as I’m still learning to get the feeling.
Let’s check the list above on our Blocky machine. Do note this is a Linux machine. While the thought process is the same for all OS’s, the things you need to look for and the tools you can use vary.
Enumerating files
I always start with looking around on the filesystem. Places I commonly look for on *nix are:
-
/home -
/opt -
/tmp -
/
When we look at Blocky, only /home seems to contain interesting files.
/opt is empty, and both /tmp and / don’t contain any files of interest.
notch@Blocky:~$ ls -alh /home/notch
total 48K
drwxr-xr-x 5 notch notch 4.0K Jul 2 2017 .
drwxr-xr-x 3 root root 4.0K Jul 2 2017 ..
-rw------- 1 notch notch 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 notch notch 220 Jul 2 2017 .bash_logout
-rw-r--r-- 1 notch notch 3.7K Jul 2 2017 .bashrc
drwx------ 2 notch notch 4.0K Jul 2 2017 .cache
drwxrwxr-x 7 notch notch 4.0K Jul 2 2017 minecraft
-rw------- 1 root root 369 Jul 2 2017 .mysql_history
drwxrwxr-x 2 notch notch 4.0K Jul 2 2017 .nano
-rw-r--r-- 1 notch notch 655 Jul 2 2017 .profile
-rw-rw-r-- 1 notch notch 66 Jul 2 2017 .selected_editor
-rw-r--r-- 1 notch notch 0 Jul 2 2017 .sudo_as_admin_successful
-r-------- 1 notch notch 32 Jul 2 2017 user.txtNormally the .bash_history file is of interest, because it contains all the commands that a user executed.
In this case however, it’s empty.
Another interesting folder is minecraft.
After going through it, it seems to be a Minecraft server without anything interesting to see.
One more thing you can see is the .sudo_as_admin_successful file.
This means that the notch user has successfully used sudo, which is used to execute commands as another user, like root.
Let’s write this one down.
Looking at the file permissions, we see a file .mysql_history which is owned by root.
This might indicate that notch used sudo to open a MySQL CLI as root.
We can also for example look for files that we own, outside of the /home directory.
notch@Blocky:~$ find / -user notch -type f ! -path "/proc/*" ! -path "/sys/*" ! -path "/home/notch/*" 2> /dev/null
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1000.slice/user@1000.service/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1000.slice/user@1000.service/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1000.slice/user@1000.service/init.scope/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1000.slice/user@1000.service/init.scope/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1000.slice/user@1000.service/init.scope/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1000.slice/user@1000.service/init.scope/notify_on_release
/tmp/libnetty-transport-native-epoll6671581788031531016.so
/tmp/hsperfdata_notch/1193This results in nothing much of interest for this box.
Last but not least, in *nix there is a SUID (Set UID) and SGID (Set GID) flag for file permissions.
This allows a user to execute a file with the permissions of the owning user or group.
If a file is owned by root, and has the SUID/SGID flag set, you can execute that file with root permissions.
By default, there are some files which have this flag set but are well protected against malicious usage.
To search for files with the SUID flag, you can execute the following command:
notch@Blocky:~$ find / -perm -4000 -type f 2>/dev/null
/bin/su
/bin/fusermount
/bin/mount
/bin/ping
/bin/umount
/bin/ping6
/bin/ntfs-3g
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/newuidmap
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/at
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-deviceTo search for files with the SGID flag, you can execute the following command:
notch@Blocky:~$ find / -perm -2000 -type f 2>/dev/null
/sbin/unix_chkpwd
/sbin/pam_extrausers_chkpwd
/usr/bin/screen
/usr/bin/ssh-agent
/usr/bin/at
/usr/bin/crontab
/usr/bin/bsd-write
/usr/bin/wall
/usr/bin/mlocate
/usr/bin/chage
/usr/bin/expiry
/usr/lib/x86_64-linux-gnu/utempter/utempterFinally, to search for files that have both the SUID and SGID flags set:
notch@Blocky:~$ find / -perm -6000 -type f 2>/dev/null
/usr/bin/atThe results that you see above are fairly standard, so nothing of interest here.
Let’s check the background jobs.
Enumerating background jobs
On *nix, crontab is the default tool for running background jobs. To show all cron jobs (background job in crontab) for the current user, run the following command:
notch@Blocky:~$ crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
@reboot cd /home/notch/minecraft && ./start.shWhen checking the content of the file /home/notch/minecraft/start.sh, we see the following:
if ! screen -list | grep blockycraft > /dev/null
then
screen -dmS blockycraft java -Xms500M -Xmx500M -jar ./sponge.jar nogui
fiHere we can see that the Minecraft server is started automatically on every reboot in a detached screen session. This could be useful, so let’s write this down.
We’re not only interested in the cron jobs of the current user, but we want to enumerate jobs of other users as well. This can partly be done with the following command:
notch@Blocky:~$ ls -alh /etc/cron.*
/etc/cron.d:
total 24K
drwxr-xr-x 2 root root 4.0K Jul 2 2017 .
drwxr-xr-x 101 root root 4.0K Jul 16 2017 ..
-rw-r--r-- 1 root root 589 Jul 16 2014 mdadm
-rw-r--r-- 1 root root 670 Mar 1 2016 php
-rw-r--r-- 1 root root 102 Apr 5 2016 .placeholder
-rw-r--r-- 1 root root 190 Jul 2 2017 popularity-contest
/etc/cron.daily:
total 60K
drwxr-xr-x 2 root root 4.0K Jul 2 2017 .
drwxr-xr-x 101 root root 4.0K Jul 16 2017 ..
-rwxr-xr-x 1 root root 539 Apr 5 2016 apache2
-rwxr-xr-x 1 root root 376 Mar 31 2016 apport
-rwxr-xr-x 1 root root 1.5K Jan 17 2017 apt-compat
-rwxr-xr-x 1 root root 355 May 22 2012 bsdmainutils
-rwxr-xr-x 1 root root 1.6K Nov 26 2015 dpkg
-rwxr-xr-x 1 root root 372 May 5 2015 logrotate
-rwxr-xr-x 1 root root 1.3K Nov 6 2015 man-db
-rwxr-xr-x 1 root root 539 Jul 16 2014 mdadm
-rwxr-xr-x 1 root root 435 Nov 18 2014 mlocate
-rwxr-xr-x 1 root root 249 Nov 12 2015 passwd
-rw-r--r-- 1 root root 102 Apr 5 2016 .placeholder
-rwxr-xr-x 1 root root 3.4K Feb 26 2016 popularity-contest
-rwxr-xr-x 1 root root 214 May 24 2016 update-notifier-common
/etc/cron.hourly:
total 12K
drwxr-xr-x 2 root root 4.0K Jul 2 2017 .
drwxr-xr-x 101 root root 4.0K Jul 16 2017 ..
-rw-r--r-- 1 root root 102 Apr 5 2016 .placeholder
/etc/cron.monthly:
total 12K
drwxr-xr-x 2 root root 4.0K Jul 2 2017 .
drwxr-xr-x 101 root root 4.0K Jul 16 2017 ..
-rw-r--r-- 1 root root 102 Apr 5 2016 .placeholder
/etc/cron.weekly:
total 24K
drwxr-xr-x 2 root root 4.0K Jul 2 2017 .
drwxr-xr-x 101 root root 4.0K Jul 16 2017 ..
-rwxr-xr-x 1 root root 86 Apr 13 2016 fstrim
-rwxr-xr-x 1 root root 771 Nov 6 2015 man-db
-rw-r--r-- 1 root root 102 Apr 5 2016 .placeholder
-rwxr-xr-x 1 root root 211 May 24 2016 update-notifier-commonDo note this doesn’t show all cron jobs scheduled by root, because they’re stored in the home directory /root.
You can see a lot of stuff in the output above.
It simply takes experience in the OS to be able to see what’s default and what is not.
A good place to start is simply Google the elements and try to understand what they do.
Next, we can check the running processes and their owner.
Enumerating running processes
To enumerate all running processes, execute the following command:
notch@Blocky:~$ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.3 0.2 37828 5920 ? Ss 11:58 0:04 /sbin/init
root 2 0.0 0.0 0 0 ? S 11:58 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 11:58 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 11:58 0:00 [kworker/0:0H]
root 7 0.0 0.0 0 0 ? S 11:58 0:00 [rcu_sched]
root 8 0.0 0.0 0 0 ? S 11:58 0:00 [rcu_bh]
root 9 0.0 0.0 0 0 ? S 11:58 0:00 [migration/0]
root 10 0.0 0.0 0 0 ? S 11:58 0:00 [watchdog/0]
root 11 0.0 0.0 0 0 ? S 11:58 0:00 [kdevtmpfs]
root 12 0.0 0.0 0 0 ? S< 11:58 0:00 [netns]
root 13 0.0 0.0 0 0 ? S< 11:58 0:00 [perf]
root 14 0.0 0.0 0 0 ? S 11:58 0:00 [khungtaskd]
root 15 0.0 0.0 0 0 ? S< 11:58 0:00 [writeback]
root 16 0.0 0.0 0 0 ? SN 11:58 0:00 [ksmd]
root 17 0.0 0.0 0 0 ? SN 11:58 0:00 [khugepaged]
root 18 0.0 0.0 0 0 ? S< 11:58 0:00 [crypto]
root 19 0.0 0.0 0 0 ? S< 11:58 0:00 [kintegrityd]
root 20 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 21 0.0 0.0 0 0 ? S< 11:58 0:00 [kblockd]
root 22 0.0 0.0 0 0 ? S< 11:58 0:00 [ata_sff]
root 23 0.0 0.0 0 0 ? S< 11:58 0:00 [md]
root 24 0.0 0.0 0 0 ? S< 11:58 0:00 [devfreq_wq]
root 28 0.0 0.0 0 0 ? S 11:58 0:00 [kswapd0]
root 29 0.0 0.0 0 0 ? S< 11:58 0:00 [vmstat]
root 30 0.0 0.0 0 0 ? S 11:58 0:00 [fsnotify_mark]
root 31 0.0 0.0 0 0 ? S 11:58 0:00 [ecryptfs-kthrea]
root 47 0.0 0.0 0 0 ? S< 11:58 0:00 [kthrotld]
root 48 0.0 0.0 0 0 ? S< 11:58 0:00 [acpi_thermal_pm]
root 49 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 50 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 51 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 52 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 53 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 54 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 55 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 56 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 57 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 58 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 59 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 60 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 61 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 62 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 63 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 64 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 65 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 66 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 67 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 68 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 69 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 70 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 71 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 72 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 73 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_0]
root 74 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_0]
root 75 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_1]
root 76 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_1]
root 82 0.0 0.0 0 0 ? S< 11:58 0:00 [ipv6_addrconf]
root 95 0.0 0.0 0 0 ? S< 11:58 0:00 [deferwq]
root 96 0.0 0.0 0 0 ? S< 11:58 0:00 [charger_manager]
root 142 0.0 0.0 0 0 ? S 11:58 0:00 [kworker/0:2]
root 145 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_2]
root 146 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_2]
root 147 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_3]
root 148 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_3]
root 149 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_4]
root 150 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_4]
root 151 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_5]
root 152 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_5]
root 153 0.0 0.0 0 0 ? S< 11:58 0:00 [kpsmoused]
root 154 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_6]
root 155 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_6]
root 156 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_7]
root 157 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_7]
root 158 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_8]
root 159 0.0 0.0 0 0 ? S< 11:58 0:00 [ttm_swap]
root 160 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_8]
root 161 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_9]
root 162 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_9]
root 163 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_10]
root 164 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_10]
root 165 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_11]
root 166 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_11]
root 168 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_12]
root 172 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_12]
root 174 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_13]
root 176 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_13]
root 181 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_14]
root 183 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_14]
root 185 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_15]
root 192 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_15]
root 193 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_16]
root 196 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_16]
root 201 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_17]
root 204 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_17]
root 207 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_18]
root 212 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_18]
root 215 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_19]
root 218 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_19]
root 219 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_20]
root 224 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_20]
root 226 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_21]
root 227 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_21]
root 229 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_22]
root 231 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_22]
root 232 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_23]
root 234 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_23]
root 235 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_24]
root 236 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_24]
root 237 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_25]
root 238 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_25]
root 239 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_26]
root 240 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_26]
root 241 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_27]
root 242 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_27]
root 243 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_28]
root 244 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_28]
root 245 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_29]
root 246 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_29]
root 247 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_30]
root 248 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_30]
root 249 0.0 0.0 0 0 ? S 11:58 0:00 [scsi_eh_31]
root 250 0.0 0.0 0 0 ? S< 11:58 0:00 [scsi_tmf_31]
root 275 0.0 0.0 0 0 ? S 11:58 0:00 [kworker/u256:28]
root 279 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 281 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 282 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 289 0.0 0.0 0 0 ? S< 11:58 0:00 [kworker/0:1H]
root 357 0.0 0.0 0 0 ? S< 11:58 0:00 [raid5wq]
root 382 0.0 0.0 0 0 ? S< 11:58 0:00 [kdmflush]
root 383 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 393 0.0 0.0 0 0 ? S< 11:58 0:00 [kdmflush]
root 394 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 410 0.0 0.0 0 0 ? S< 11:58 0:00 [bioset]
root 438 0.0 0.0 0 0 ? S 11:58 0:00 [jbd2/dm-0-8]
root 439 0.0 0.0 0 0 ? S< 11:58 0:00 [ext4-rsv-conver]
root 508 0.0 0.1 29728 3132 ? Ss 11:58 0:00 /lib/systemd/systemd-journald
root 518 0.0 0.0 0 0 ? S 11:58 0:00 [kauditd]
root 520 0.0 0.0 102972 1620 ? Ss 11:58 0:00 /sbin/lvmetad -f
root 540 0.0 0.2 44776 4252 ? Ss 11:58 0:00 /lib/systemd/systemd-udevd
root 651 0.0 0.0 0 0 ? S< 11:58 0:00 [iscsi_eh]
root 653 0.0 0.0 0 0 ? S< 11:58 0:00 [ib_addr]
root 658 0.0 0.0 0 0 ? S< 11:58 0:00 [ib_mcast]
root 660 0.0 0.0 0 0 ? S< 11:58 0:00 [ib_nl_sa_wq]
root 663 0.0 0.0 0 0 ? S< 11:58 0:00 [ib_cm]
root 664 0.0 0.0 0 0 ? S< 11:58 0:00 [iw_cm_wq]
root 675 0.0 0.0 0 0 ? S< 11:58 0:00 [rdma_cm]
root 832 0.0 0.0 0 0 ? S< 11:58 0:00 [ext4-rsv-conver]
systemd+ 865 0.0 0.1 100328 2528 ? Ssl 11:58 0:00 /lib/systemd/systemd-timesyncd
root 1094 0.0 0.1 29012 2960 ? Ss 11:58 0:00 /usr/sbin/cron -f
root 1097 0.0 0.0 4404 1320 ? Ss 11:58 0:00 /usr/sbin/acpid
root 1100 0.0 0.4 185616 9764 ? Ssl 11:58 0:01 /usr/bin/vmtoolsd
root 1106 0.0 1.0 201616 20936 ? Ssl 11:58 0:00 /usr/lib/snapd/snapd
root 1107 0.0 0.1 28552 3132 ? Ss 11:58 0:00 /lib/systemd/systemd-logind
root 1114 0.0 0.4 275876 8328 ? Ssl 11:58 0:00 /usr/lib/accountsservice/accounts-daemon
syslog 1119 0.0 0.1 256400 3292 ? Ssl 11:58 0:00 /usr/sbin/rsyslogd -n
root 1126 0.1 0.2 613468 5840 ? Ssl 11:58 0:02 /usr/bin/lxcfs /var/lib/lxcfs/
message+ 1127 0.0 0.1 42904 3724 ? Ss 11:58 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation
daemon 1152 0.0 0.1 26048 2176 ? Ss 11:58 0:00 /usr/sbin/atd -f
notch 1165 0.0 0.1 27192 2748 ? Ss 11:58 0:00 screen -dmS blockycraft java -Xms500M -Xmx500M -jar ./sponge.jar nogui
root 1175 0.0 0.3 277184 6140 ? Ssl 11:58 0:00 /usr/lib/policykit-1/polkitd --no-debug
notch 1193 8.8 29.1 2495664 591744 pts/0 Ssl+ 11:58 1:54 java -Xms500M -Xmx500M -jar ./sponge.jar nogui
root 1194 0.0 0.0 13380 168 ? Ss 11:58 0:00 /sbin/mdadm --monitor --pid-file /run/mdadm/monitor.pid --daemonise --scan --syslog
root 1312 0.0 0.2 65524 5256 ? Ss 11:58 0:00 /usr/sbin/sshd -D
root 1341 0.0 1.4 286020 28700 ? Ss 11:58 0:00 php-fpm: master process (/etc/php/7.0/fpm/php-fpm.conf)
root 1363 0.0 0.0 5228 160 ? Ss 11:58 0:00 /sbin/iscsid
root 1364 0.0 0.1 5728 3524 ? S<Ls 11:58 0:00 /sbin/iscsid
mysql 1401 0.0 7.7 1116064 157948 ? Ssl 11:58 0:00 /usr/sbin/mysqld
root 1431 0.0 0.0 15944 1860 tty1 Ss+ 11:58 0:00 /sbin/agetty --noclear tty1 linux
www-data 1464 0.0 0.3 286020 7272 ? S 11:58 0:00 php-fpm: pool www
www-data 1465 0.0 0.3 286020 7272 ? S 11:58 0:00 php-fpm: pool www
proftpd 1466 0.0 0.1 119644 3560 ? Ss 11:58 0:00 proftpd: (accepting connections)
root 1520 0.0 1.4 325600 28896 ? Ss 11:58 0:00 /usr/sbin/apache2 -k start
www-data 1523 0.0 0.4 325624 8736 ? S 11:58 0:00 /usr/sbin/apache2 -k start
www-data 1524 0.0 0.4 325624 8736 ? S 11:58 0:00 /usr/sbin/apache2 -k start
www-data 1525 0.0 0.4 325624 8736 ? S 11:58 0:00 /usr/sbin/apache2 -k start
www-data 1526 0.0 0.4 325624 8736 ? S 11:58 0:00 /usr/sbin/apache2 -k start
www-data 1527 0.0 0.4 325624 8736 ? S 11:58 0:00 /usr/sbin/apache2 -k start
root 1595 0.0 0.3 95408 6992 ? Ss 11:59 0:00 sshd: notch [priv]
notch 1597 0.0 0.2 45368 4540 ? Ss 11:59 0:00 /lib/systemd/systemd --user
notch 1599 0.0 0.0 61280 2008 ? S 11:59 0:00 (sd-pam)
notch 1674 0.0 0.2 95608 4268 ? S 11:59 0:00 sshd: notch@pts/1
notch 1675 0.0 0.2 22584 5340 pts/1 Ss 11:59 0:00 -bash
root 1784 0.0 0.0 0 0 ? S 12:09 0:00 [kworker/0:0]
root 1786 0.0 0.0 0 0 ? S 12:09 0:00 [kworker/u256:0]
notch 1816 0.0 0.1 37368 3340 pts/1 R+ 12:20 0:00 ps -auxHere we can see a few interesting things:
-
notch 1165 0.0 0.1 27192 2748 ? Ss 11:58 0:00 screen -dmS blockycraft java -Xms500M -Xmx500M -jar ./sponge.jar nogui -
notch 1193 8.8 29.1 2495664 591744 pts/0 Ssl+ 11:58 1:54 java -Xms500M -Xmx500M -jar ./sponge.jar nogui -
proftpd 1466 0.0 0.1 119644 3560 ? Ss 11:58 0:00 proftpd: (accepting connections) -
www-data 1523 0.0 0.4 325624 8736 ? S 11:58 0:00 /usr/sbin/apache2 -k start -
mysql 1401 0.0 7.7 1116064 157948 ? Ssl 11:58 0:00 /usr/sbin/mysqld
The first two processes are the result of the cron job we found for Notch.
We already saw ProFTPD was listening on port 21 in our Exploration step. Here we can see the running process which is owned by user proftpd.
It is best practice to run network processes as a dedicated user to decrease the attack surface[3], so this is configured correctly.
Same with the Apache and MySQL processes.
Now we’ve identified the running processes, let’s see if there are interesting open ports that we haven’t seen yet.
Enumerating open ports
To check for open ports, you can run the following command:
notch@Blocky:~/minecraft$ netstat -antup
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 604 10.10.10.37:22 10.10.14.7:49472 ESTABLISHED -
tcp 0 0 10.10.10.37:22 10.10.14.7:54162 ESTABLISHED -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -We can see that there’s a running MySQL instance listening on localhost on port 3306, which isn’t accessible remotely. Also, we can see there are active SSH sessions from my machine. Nothing interesting though.
Next up, let’s check our OS and kernel versions.
Enumerating OS and kernel versions
To check the OS version:
notch@Blocky:~$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.2 LTS
Release: 16.04
Codename: xenialTo check the kernel version:
notch@Blocky:~$ uname -a
Linux Blocky 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/LinuxNow the question is: what can we do with this information? Like we did with the network services; checking for known vulnerabilities. Interesting categories are for example Remote Code Execution and of course Privilege Escalation.
Known vulnerabilities for Linux kernel 4.4.0[4]:
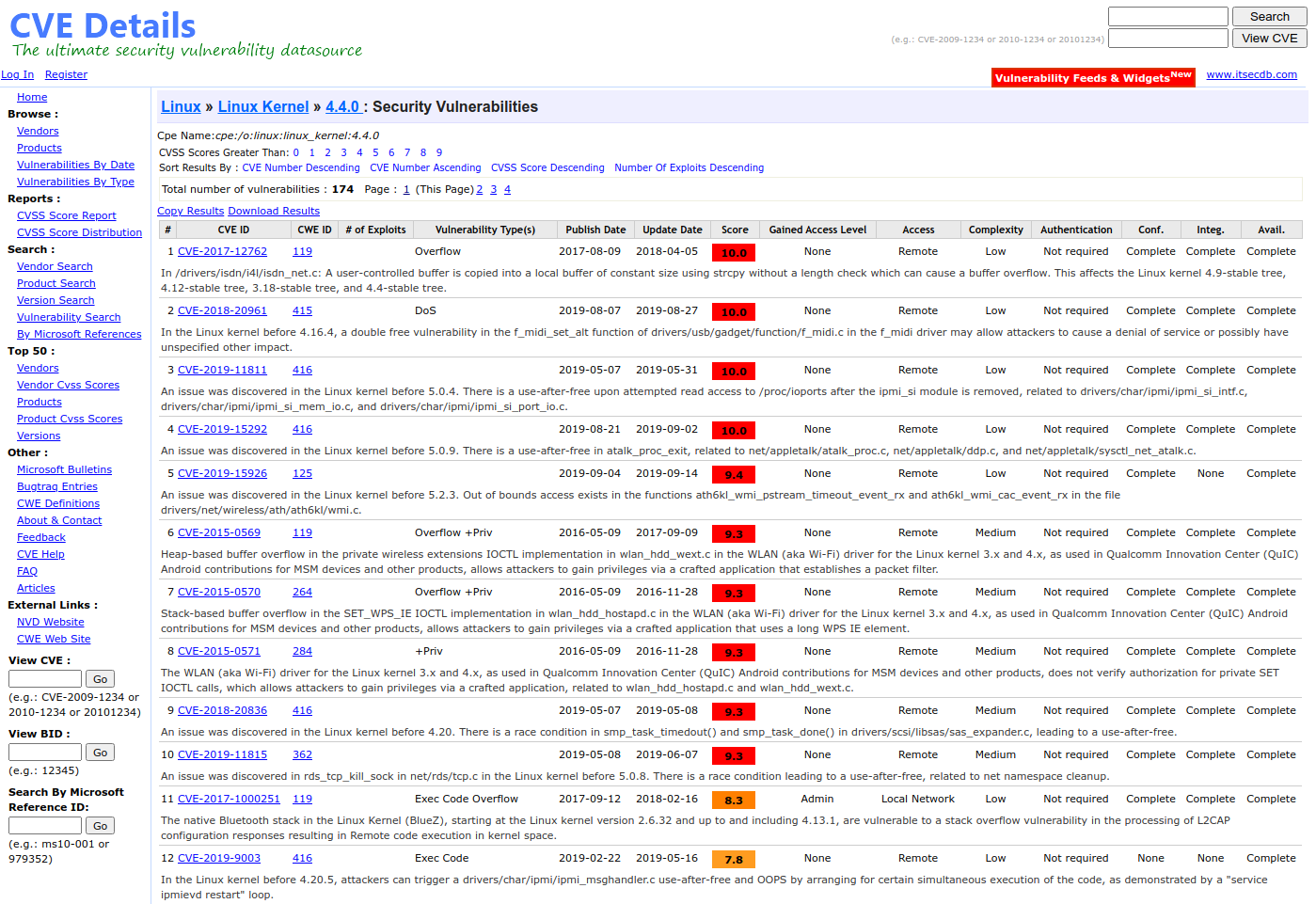
If we broaden the scope even more by searching for Ubuntu 16.04.2, we see even more vulnerabilities. The page lists a total of 1132(!) vulnerabilities, although most of these vulnerabilities will probably be solved in one of the patch releases since we’re on 16.04.2 (and the page lists 16.04).
Last, but not least, let’s check our privileges.
Enumerating privileges
With *nix, one of the things you always need to check are the sudo rights.
You can do so with the following command:
notch@Blocky:~/minecraft$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALLIf a hacker sees the output above, he/she would be very happy.
This means we can use sudo to run any command as root.
Looking back at our results when enumerating the files, we already saw two hints towards the sudo usage.
We saw the file .sudo_as_admin_successful, and the root file .mysql_history.
This is the first thing I would try in our next step: Privilege Escalation.
Summarizing
We’ve gone through just the basics of enumeration, but even now we’ve seen a lot of information already. This is the reason why it’s so important to write everything down in a structured way and to store the results of all your commands. If you write everything down, it’s a lot easier to search across your results. When you forget the password for user X for example, you can simply search in your notes instead of exploiting the same vulnerability again. An even bigger advantage is you’re building a manual for yourself on how to go through certain services to find the needle in the haystack. This has helped me a lot when going through the boxes in Hack The Box.
Now, let’s summarize what we’ve seen thus far which might be interesting for our next step:
-
A Minecraft server is started on every reboot in a screen session under user
notch, which is a Java application -
User Notch has used
sudobefore, and might’ve started a MySQL CLI session asrootwith it -
A MySQL server is listening on port 3306 on localhost, which is running as user
mysql -
There might be some vulnerabilities in the OS or kernel that we can use
-
We can execute any command as any user with
sudo
What’s next
This was the step on Enumeration.
The next step is Privilege Escalation, in which we use the information gathered from all previous steps to try to gain root access.
This however is good for another blog post!
See you next time?
